A Cyber Threat Assessment is crucial for identifying vulnerabilities and securing your business against emerging cyber threats. It enables proactive risk mitigation by identifying weaknesses before they can be exploited by attackers. The assessment strengthens both internal and external defences, ensuring comprehensive protection for your organisation. Additionally, it helps ensure regulatory compliance, providing the insights needed to meet industry-specific security standards. With detailed findings, a Cyber Threat Assessment empowers you to make informed decisions about security investments and improvements, helping you build a stronger security posture.
Why Our Cyber Threat Assessment Stands Out
-
Non-Intrusive: We identify vulnerabilities and weaknesses in your systems without exploiting them, ensuring that your operations remain unaffected throughout the assessment. Our approach focuses on thorough risk identification, avoiding disruptions to your business processes while delivering actionable insights.
-
Attack Surface Analysis: Our assessment provides a comprehensive view of your organisation’s attack surface—both internally and externally. We evaluate all potential entry points, including network infrastructures, web applications, and employee behaviours, to give you a clear understanding of your overall exposure to cyber threats.
-
Tailored Threat Models: We create custom threat models based on your organisation’s specific infrastructure, business processes, and industry. This targeted approach helps us to identify the most relevant risks and recommend practical, effective strategies to mitigate those threats, ensuring that your security efforts are aligned with your unique needs.
-
Expert Recommendations: Our team of seasoned cybersecurity professionals provides you with actionable recommendations that are specifically tailored to your environment. These insights not only address current vulnerabilities but also offer guidance on strengthening your security posture over time, helping you stay ahead of evolving cyber threats.
Cyber Threat Assessment Framework
Our Cyber Threat Assessment follows a structured, thorough process designed to identify and mitigate risks across your organisation. We work closely with you at every step to ensure that we provide actionable insights that strengthen your security posture.
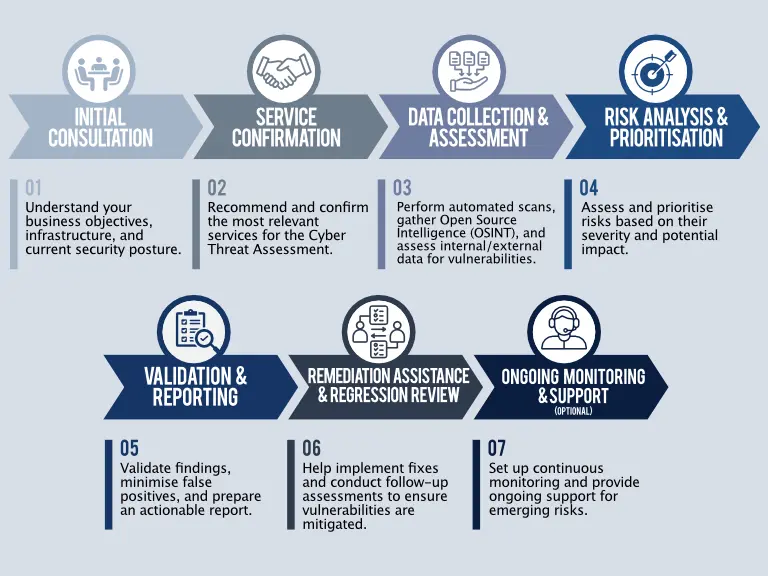
Our Cyber Threat Assessment Services
We offer a comprehensive range of cyber threat assessment services designed to proactively identify, evaluate, and mitigate risks posed by various attack vectors to your organisation’s security.
Social Engineering Assessment
- Test your organisation’s resilience to social engineering attacks, including phishing, pretexting, and baiting.
- Simulate real-world attack scenarios to assess the effectiveness of employee awareness and response to manipulation tactics.
- Evaluate the security of communication channels, including email, phone, and social media platforms.
- Identify vulnerabilities in human behaviour and provide training recommendations to strengthen your security culture.
- Deliver a detailed findings, recommendations, and best practices for mitigating social engineering risks.
OSINT Assessment
- Conduct an open-source intelligence (OSINT) assessment to uncover publicly available information that could be leveraged by attackers.
- Assess the exposure of your organisation’s sensitive data, employee details, and organisational structure on the web.
- Review the security of your social media presence and online footprint to identify potential data leakage or privacy risks.
- Simulate how threat actors might gather and exploit OSINT for reconnaissance before launching an attack.
- Provide actionable recommendations to reduce online visibility and limit potential attack vectors.
External Network Vulnerability Assessment
- Assess your organisation’s external-facing systems, including websites, servers, and networks, for vulnerabilities.
- Identify open ports, outdated software, misconfigurations, and other potential entry points for attackers.
- Conduct both automated and manual testing to uncover hidden vulnerabilities and evaluate overall security posture.
- Simulate real-world attack scenarios to test your defences against common external threats such as DDoS, SQL injection, and cross-site scripting (XSS).
- Provide detailed vulnerabilities and recommendations for remediation and risk mitigation.
Internal Network Vulnerability Assessment
- Assess the security of your internal network and systems by simulating an attacker with internal access.
- Identify weaknesses in your network architecture, access control policies, and user privilege configurations.
- Test for vulnerabilities in internal applications, databases, and devices that could be exploited by insiders or compromised users.
- Evaluate the effectiveness of internal monitoring, logging, and incident detection systems.
- Provide actionable insights to strengthen internal security measures and prevent lateral movement and data breaches within your organisation.



