Application Security Assessment is essential for businesses looking to ensure the security of their applications—whether web, mobile, or APIs. With the growing number of cyber threats targeting applications, it is crucial to proactively assess and strengthen their security posture.
Our Application Security Assessment solution helps you identify vulnerabilities across your applications and infrastructure, providing actionable insights to secure your web and mobile applications, APIs, and web services. We follow OWASP standards and industry best practices to ensure your applications are resistant to exploitation and that your development processes are secure. With a strong focus on DevSecOps, our solution integrates security at every stage of the software development lifecycle.
Why Our Application Security Assessment Stands Out
- Comprehensive Application Coverage: We assess a wide range of applications, including web applications, mobile apps, APIs, and web services, ensuring all potential vulnerabilities are identified.
- OWASP-Based Testing: Our testing is aligned with OWASP’s Top 10 security risks, which represent the most common and critical security flaws in web applications.
- Manual and Automated Testing: We combine both automated scans and manual penetration testing to ensure that no vulnerability is overlooked, providing a thorough assessment of your applications.
- Secure Coding Best Practices: We ensure your development teams are equipped with the knowledge to follow secure coding practices, reducing the likelihood of introducing vulnerabilities in future releases.
- Actionable Insights and Support: We provide a detailed report with clear recommendations and remediation support, helping you strengthen your application security and protect your users.
Application Security Assessment Framework
Our Application Security Assessment follows a structured process designed to evaluate and enhance the security of your applications and infrastructure. We assess the technical elements of your security posture, identifying vulnerabilities that could be exploited by attackers.
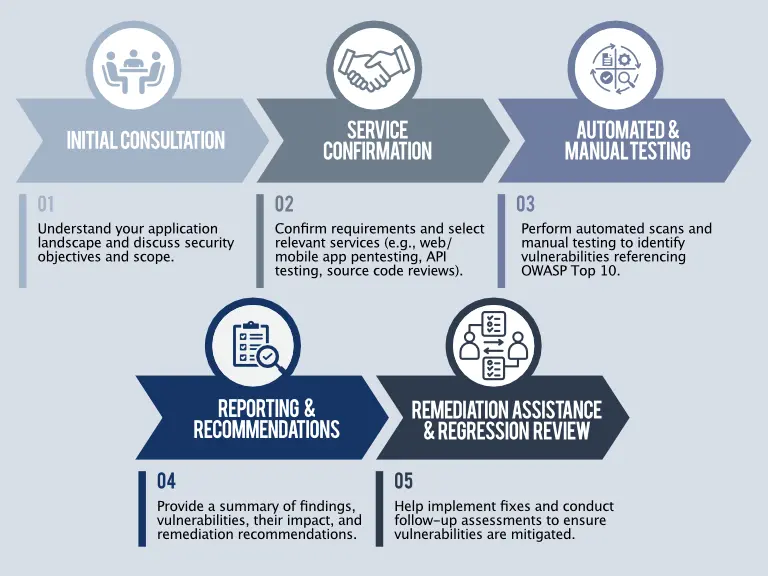
Our Application Security Assessment Services
We offer a range of Application Security Assessment services designed to identify and address vulnerabilities in various areas of your application infrastructure.
Web Application Penetration Testing
- Identify vulnerabilities in web applications through comprehensive testing.
- Conduct assessments based on the OWASP Top 10 to address critical risks.
- Test for common vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF).
- Simulate real-world attacks to uncover business logic flaws and other advanced threats.
- Provide detailed findings with actionable remediation steps to secure your application.
Mobile Application Penetration Testing
- Assess the security posture of mobile apps on Android and iOS platforms.
- Test for data leakage, insecure APIs, weak cryptography, and other mobile-specific vulnerabilities.
- Analyse mobile app source code and reverse engineering risks.
- Evaluate the security of app-to-backend communications to prevent interception.
- Provide security hardening recommendations to ensure secure mobile app deployment.
Web Services Penetration Testing
- Test the security of web services such as REST, SOAP, and GraphQL APIs.
- Review authentication mechanisms, including OAuth, API tokens, and basic auth.
- Assess data validation and input sanitisation to protect against injection attacks.
- Evaluate security controls for rate limiting, logging, and abuse prevention.
- Provide comprehensive findings with risk analysis and practical recommendations.
External Network Penetration Testing
- Simulate external attacks to assess the security of your organisation’s perimeter.
- Test for open ports, unpatched vulnerabilities, and misconfigurations in external-facing systems.
- Analyse firewall configurations and evaluate the effectiveness of network security controls.
- Attempt to bypass network defences to assess real-world risk.
- Deliver detailed vulnerability findings with clear remediation steps to reduce exposure.
Internal Network Penetration Testing
- Assess the security of your internal network by simulating an attacker with internal access.
- Test for misconfigured access controls, weak passwords, and privilege escalation opportunities.
- Evaluate lateral movement opportunities within the internal network.
- Identify insider threats and potential data leaks from compromised systems.
- Provide remediation recommendations to reduce the risk of internal attacks and data breaches.



